Learn What is Phishing and save your money from Hackers

Phishing is an attempt to criminally and fraudulently acquire sensitive information, such as usernames, passwords and credit card details, by appearing as a trustworthy entity in an electronic communication. eBay, PayPal and other online banks are common targets. Phishing is typically carried out by email or instant messaging and often directs users to enter details at a website, although phone contact has also been used. Phishing is an example of social engineering techniques used to fool users.Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical measures.
Recent phishing attempts have targeted the customers of banks and online payment services.Social networking sites such as Orkut are also a target of phishing.
Spoofed/Fraudulent e-mails are the most widely used tools to carry out the phishing attack.In most cases we get a fake e-mail that appears to have come from a Trusted Website . Here the hacker may request us to verify username & password by replaying to a given email address.
TECHNIQUES BEHIND PHISHING ATTACK
1.Link Manipulation
Most methods of phishing use some form of technical deception designed to make a link in an email appear to belong to some trusted organization or spoofed organization. Misspelled URLs or the use of subdomains are common tricks used by phishers, such as this example URL
www.micosoft.com
www.mircosoft.com
www.verify-microsoft.com
Instead of http://www.microsoft.com/
2.Filter Evasion
Phishers have used images instead of text to make it harder for anti-phishing filters to detect text commonly used in phishing emails.This is the reason Gmail or Yahoo will disable the images by default for incoming mails.
How does a phishing attack/scam look like?
As scam artists become more sophisticated, so do their phishing e-mail messages and pop-up windows.They often include official-looking logos from real organizations and other identifying information taken directly from legitimate Web sites.Here is an example of how the phishing scam email looks like

Example of a phishing e-mail message, including a deceptive URL address linking to a scam Web site.
To make these phishing e-mail messages look even more legitimate, the scam artists may place a link in them that appears to go to the legitimate Web site (1), but it actually takes you to a phishing site (2) or possibly a pop-up window that looks exactly like the official site.
These copycat sites are also called “spoofed” Web sites. Once you’re at one of these spoofed sites, you may send personal information to the hackers.
How to identify a fraudulent e-mail?
Here are a few phrases to look for if you think an e-mail message is a phishing scam.
“Verify your account.”
Legitimate sites will never ask you to send passwords, login names, Social Security numbers, or any other personal information through e-mail.
“If you don’t respond within 48 hours, your account will be closed.”
These messages convey a sense of urgency so that you’ll respond immediately without thinking.
“Dear Valued Customer.”
Phishing e-mail messages are usually sent out in bulk and often do not contain your first or last name.
“Click the link below to gain access to your account.”
HTML-formatted messages can contain links or forms that you can fill out just as you’d fill out a form on a Web site. The links that you are urged to click may contain all or part of a real company’s name and are usually “masked,” meaning that the link you see does not take you to that address but somewhere different, usually a scam Web site.
Notice in the following example that resting the mouse pointer on the link reveals the real Web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company’s Web address, which is a suspicious sign.

So the Bottom line to defend from phishing attack is-
1.Never assume that an email is valid based on the sender’s email address.
2.A trusted bank/organization such as paypal will never ask you for your full name and password in a PayPal email.
3.An email from trusted organization will never contain attachments or software.
4.Clicking on a link in an email is the most insecure way to get to your account.
By:sukak2r2
Installing VMWare Workstation 6.5.2 On BackTrack 4
As usual, brand new kernel woes with VMware. Here’s a quick way to patch up VMware 6.5.2 to get the modules to compile. Start by downloading and installing VMWare Workstation 6.5.2.

Once that’s done, run the following commands:
rmmod kvm_intel kvm
echo blacklist kvm >> /etc/modprobe.d/blacklist
cd /tmp
wget www.offensive-security.com/tools/bt4-vmware-workstation-patch.tar.bz2
tar jxpf bt4-vmware-workstation-patch.tar.bz2
chmod 755 vmware-6.5.2-modules-2.6.29-fix*
./vmware-6.5.2-modules-2.6.29-fix.sh
vmware-modconfig –console –install-all
vmware
Done!
Source: Offensive SecurityThis is the way a system is hacked using Exploits
Exploit is a code built in C, VB etc.. that takes advantage of an open port.
This guide will teach you how to hack into a computer without sending any trojan server in other words - using Exploits..
In the following steps i'll show you how to hack into a computer using a port 5000 exploit, but you can do the same for other ports just download there exploit from:
- Google.com
- Securiteam.com
- K-otik.com
- Astalavista.box.sk
- Coromputer.net
- Securityfocus.com
(Search the exploit as: "Exploit for PORT NUMBER")
STEP 1: Download port 5000 exploit, uslly the exploits come as .txt and you need to change them to .c
http://planet.nana.co.il/progroup/exploits/5000e.zip
After downloading and extracting the port 5000 Exploit we need to compile it (covert it to .exe), In order to compile the exploit we need the "Cygwin" program.
http://sources.redhat.com/cygwin/setup.exe
STEP 2: Open the Cygwin setup.exe and install it by the following pictures:










STEP 3: After installing the program we need to compile the exploit, place the 5000.c exploit in C:\cygwin\bin
then run the command line from - Start - Run - cmd/command
in the command window type:
CD c:\cygwin\bin
gcc 5000.c -o 5000.exe
(CD = Open)
Or follow by the picture:

STEP 4: After we finshed to compiled the exploit we can use it! =)
in order to connect the the victims computer that has port 5000 open in this case..
Open the command line by - Start - Run
then type:
CD c:\cygwin\bin
5000.exe XXX.XXX.XXX.XXX -e
(XXX.XXX.XXX.XXX = Victims IP address)
Or follow by the picture:

Source: hxxp://prorat.net/forum/viewtopic.php?t=1838
Basic Entry into a WEP Encrypted Network
1. Getting the right tools
Download Backtrack 3. It can be found here:
http://www.remote-exploit.org/backtrack_download.html
The Backtrack 4 beta is out but until it is fully tested (especially if you are a noob) I would get the BT3 setup. The rest of this guide will proceed assuming you downloaded BT3. I downloaded the CD iso and burned it to a cd. Insert your BT3 cd/usb drive and reboot your computer into BT3. I always load into the 3rd boot option from the boot menu. (VESA/KDE) You only have a few seconds before it auto-boots into the 1st option so be ready. The 1st option boots too slowly or not at all so always boot from the 2nd or 3rd. Experiment to see what works best for you.
2. Preparing the victim network for attack
Once in BT3, click the tiny black box in the lower left corner to load up a "Konsole" window. Now we must prep your wireless card.
Type:
airmon-ng
You will see the name of your wireless card. (mine is named "ath0") From here on out, replace "ath0" with the name of your card.
Now type:
airmon-ng stop ath0
then type:
ifconfig wifi0 down
then:
macchanger --mac 00:11:22:33:44:55 wifi0
then:
airmon-ng start wifi0
What these steps did was to spoof (fake) your mac address so that JUST IN CASE your computers discovered by someone as you are breaking in, they will not see your REAL mac address. Moving on...
Now it's time to discover some networks to break into.
Type:
airodump-ng ath0
Now you will see a list of wireless networks start to populate. Some will have a better signal than others and it is a good idea to pick one that has a decent signal otherwise it will take forever to crack or you may not be able to crack it at all.
Once you see the network that you want to crack, do this:
hold down ctrl and tap c
This will stop airodump from populating networks and will freeze the screen so that you can see the info that you need.
**Now from here on out, when I tell you to type a command, you need to replace whatever is in parenthesis with what I tell you to from your screen. For example: if i say to type:
-c (channel)
then don't actually type in
-c (channel)
Instead, replace that with whatever the channel number is...so, for example you would type:
-c 6
Can't be much clearer than that...lets continue...
Now find the network that you want to crack and MAKE SURE that it says the encryption for that network is WEP. If it says WPA or any variation of WPA then move on...you can still crack WPA with backtrack and some other tools but it is a whole other ball game and you need to master WEP first.
 Once you've decided on a network, take note of its channel number and bssid. The bssid will look something like this --> 05:gk:30:fo:s9:2n
Once you've decided on a network, take note of its channel number and bssid. The bssid will look something like this --> 05:gk:30:fo:s9:2nThe Channel number will be under a heading that says "CH".
Now, in the same Konsole window, type:
airodump-ng -c (channel) -w (file name) --bssid (bssid) ath0
the FILE NAME can be whatever you want. This is simply the place that airodump is going to store the packets of info that you receive to later crack. You don't even put in an extension...just pick a random word that you will remember. I usually make mine "wepkey" because I can always remember it.
**Side Note: if you crack more than one network in the same session, you must have different file names for each one or it won't work. I usually just name them wepkey1, wepkey2, etc.
Once you typed in that last command, the screen of airodump will change and start to show your computer gathering packets. You will also see a heading marked "IV" with a number underneath it. This stands for "Initialization Vector" but in noob terms all this means is "packets of info that contain clues to the password." Once you gain a minimum of 5,000 of these IV's, you can try to crack the password. I've cracked some right at 5,000 and others have taken over 60,000. It just depends on how long and difficult they made the password.
Now you are thinking, "I'm screwed because my IV's are going up really slowly." Well, don't worry, now we are going to trick the router into giving us HUNDREDS of IV's per second.
3. Actually cracking the WEP password
Now leave this Konsole window up and running and open up a 2nd Konsole window. In this one type:
aireplay-ng -1 0 -a (bssid) -h 00:11:22:33:44:55 ath0
 This will send some commands to the router that basically cause it to associate with your computer even though you are not officially connected with the password. If this command is successful, you should see about 4 lines of text print out with the last one saying something similar to "Association Successful :-)" If this happens, then good! You are almost there. Now type:
This will send some commands to the router that basically cause it to associate with your computer even though you are not officially connected with the password. If this command is successful, you should see about 4 lines of text print out with the last one saying something similar to "Association Successful :-)" If this happens, then good! You are almost there. Now type:aireplay-ng -3 -b (bssid) -h 00:11:22:33:44:55 ath0
 This will generate a bunch of text and then you will see a line where your computer is gathering a bunch of packets and waiting on ARP and ACK. Don't worry about what these mean...just know that these are your meal tickets. Now you just sit and wait. Once your computer finally gathers an ARP request, it will send it back to the router and begin to generate hundreds of ARP and ACK per second. Sometimes this starts to happen within seconds...sometimes you have to wait up to a few minutes. Just be patient. When it finally does happen, switch back to your first Console window and you should see the number underneath the IV starting to rise rapidly. This is great! It means you are almost finished! When this number reaches AT LEAST 5,000 then you can start your password crack. It will probably take more than this but I always start my password cracking at 5,000 just in case they have a really weak password.
This will generate a bunch of text and then you will see a line where your computer is gathering a bunch of packets and waiting on ARP and ACK. Don't worry about what these mean...just know that these are your meal tickets. Now you just sit and wait. Once your computer finally gathers an ARP request, it will send it back to the router and begin to generate hundreds of ARP and ACK per second. Sometimes this starts to happen within seconds...sometimes you have to wait up to a few minutes. Just be patient. When it finally does happen, switch back to your first Console window and you should see the number underneath the IV starting to rise rapidly. This is great! It means you are almost finished! When this number reaches AT LEAST 5,000 then you can start your password crack. It will probably take more than this but I always start my password cracking at 5,000 just in case they have a really weak password.Now you need to open up a 3rd and final Konsole window. This will be where we actually crack the password. Type:
aircrack-ng -b (bssid) (filename)-01.cap
Remember the file name you made up earlier? Mine was "wepkey". Don't put a space in between it and -01.cap here. Type it as you see it. So for me, I would type wepkey-01.cap
Once you have done this you will see aircrack fire up and begin to crack the password. typically you have to wait for more like 10,000 to 20,000 IV's before it will crack. If this is the case, aircrack will test what you've got so far and then it will say something like "not enough IV's. Retry at 10,000." DON'T DO ANYTHING! It will stay running...it is just letting you know that it is on pause until more IV's are gathered. Once you pass the 10,000 mark it will automatically fire up again and try to crack it. If this fails it will say "not enough IV's. Retry at 15,000." and so on until it finally gets it.
 If you do everything correctly up to this point, before too long you will have the password! now if the password looks goofy, dont worry, it will still work. some passwords are saved in ASCII format, in which case, aircrack will show you exactly what characters they typed in for their password. Sometimes, though, the password is saved in HEX format in which case the computer will show you the HEX encryption of the password. It doesn't matter either way, because you can type in either one and it will connect you to the network.
If you do everything correctly up to this point, before too long you will have the password! now if the password looks goofy, dont worry, it will still work. some passwords are saved in ASCII format, in which case, aircrack will show you exactly what characters they typed in for their password. Sometimes, though, the password is saved in HEX format in which case the computer will show you the HEX encryption of the password. It doesn't matter either way, because you can type in either one and it will connect you to the network.Take note, though, that the password will always be displayed in aircrack with a colon after every 2 characters. So for instance if the password was "secret", it would be displayed as:
se:cr:et
This would obviously be the ASCII format. If it was a HEX encrypted password that was something like "0FKW9427VF" then it would still display as:
0F:KW:94:27:VF
Just omit the colons from the password, boot back into whatever operating system you use, try to connect to the network and type in the password without the colons and presto! You are in!
It may seem like a lot to deal with if you have never done it, but after a few successful attempts, you will get very quick with it. If I am near a WEP encrypted router with a good signal, I can often crack the password in just a couple of minutes.
I am not responsible for what you do with this information. Any malicious/illegal activity that you do, falls completely on you because...technically...this is just for you to test the security of your own network. :-)
I will gladly answer any legitimate questions anyone has to the best of my ability.
HOWEVER, I WILL NOT ANSWER ANYONE THAT IS TOO LAZY TO READ THE WHOLE TUT AND JUST ASKS ME SOME QUESTION THAT I CLEARLY ANSWERED. No one wants to hold your hand through this...read the tut and go experiment until you get it right.
There are rare occasions where someone will use WEP encryption with SKA as well. (Shared Key Authentication) If this is the case, additional steps are needed to associate with the router and therefore, the steps I lined out here will not work. I've only seen this once or twice, though, so you probably won't run into it. If I get motivated, I may throw up a tut on how to crack this in the future.
Credits to :
Tutori4L by :kumalynx
Picture ; edit Phr4ses By Speci4L Security Te4m

CyberXP Dark Edition V1 | 810 MB
Soucre........... Windows XP Professional
Release Name..... CyberXP Dark Edition
File Name........ CyberXP Dark Edition [v1]
Service Pack..... 3
Product Key...... NOT NEEDED
WGA.............. CRACKED
Genuine.......... Yes
Creater.......... Jcberry526
ISO Size......... 810MB
RAR Size......... 768MB
ISO FILE MD-5.... 776a5e6b35abeb8b7ea54da195b81ead
TWEAKS:
There has been about 30/40 reg tweaks done
THEMES:
5 Windows XP (Dark) themes added
SILENT ADDONS (PRE-INSTALLED):
- Internet Explorer 8
- Windows Media Player 11
- VLC Player
- WinRAR
- UniExtract
- PowerISO
- Notepad+
- NNS Genuine
- NET. Framework (All-In-One)
- LClock
- Klite Codec Pack
- Java 6
- Firefox 3.0.11
- DVD Shrink
- DVDFab
- ConvertXtoDVD
- CCleaner
- adobe Reader
- Adobe Flash Player
EXTRA ADDONS (NOT PRE-INSTALLED):
- Rainbar
- Styler
- TranBar
- TrueTransparency
- ViOrb
- ViStart
- Visual TaskTip
- WinFlip
http://rapidshare.com/files/246501741/CXP-DE-V1.part01.rar
http://rapidshare.com/files/246501951/CXP-DE-V1.part02.rar
http://rapidshare.com/files/246502077/CXP-DE-V1.part03.rar
http://rapidshare.com/files/246502188/CXP-DE-V1.part04.rar
http://rapidshare.com/files/246502436/CXP-DE-V1.part05.rar
http://rapidshare.com/files/246502461/CXP-DE-V1.part06.rar
http://rapidshare.com/files/246502665/CXP-DE-V1.part07.rar
http://rapidshare.com/files/246502775/CXP-DE-V1.part08.rar
Change XP D3skt0p Icons Into Smaller List View
Has it ever bothered you that you can’t change the size of the icons on your XP desktop? Thankfully they added this ability into Windows Vista, but what are your options in the meantime? There’s a small utility called Deskview that lets you change the icons from regular mode into the smaller “list” mode with a double-click. It’s as simple as that. Download and extract the zipfile, and then double-click on deskview.exe, and your icons will turn from this:

~~Download
backtrack 4 pre-release
Date: Fri, 19 Jun 2009 23:02:32 -0400
From: Mati Aharoni <muts@offensive-security.com>
Subject: [Full-disclosure] BackTrack 4 Pre Release Available for
Download
To: full-disclosure@lists.grok.org.uk
Message-ID:
<8b0e09fc0906192002o2db466d2hecbbfe127211f89@mail.gmail.com>
Content-Type: text/plain; charset=ISO-8859-1
Dear Everyone,
The Remote Exploit team is ecstatic to announce the availability of
BackTrack 4 Pre Release.
BackTrack 4 has undergone many changes - find more about it here :
http://www.offensive-security.com/backtrack4-guide-tutorial.pdf
You can download backtrack 4 pre final here:
http://www.remote-exploit.org/cgi-bin/fileget?version=bt4-prefinal-iso
If you would like to link to BackTrack, please use the remote-exploit
link above.
Check our Pre Release Blog announcement:
http://www.offensive-security.com/blog/backtrack/backtrack-pre-final-public-release-and-download/
May the sauce be with you,
Remote Exploit Team
Knowledge of open access with port and protection from penetration
| X-NetStat Professional Program Features: | |
|
|
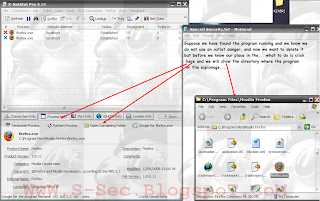
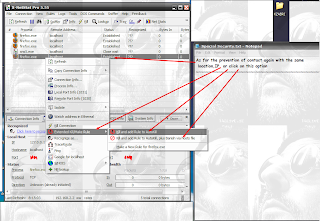
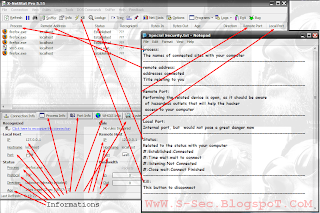
Rar Pass:S-sec.BlogSpoT.coM
+ Added Google search buttons next to remote IP and hostname
+ Added -stealth command line parameter to run the program completely hidden.
+ Added -shutdown command line parameter to shut down the program.
+ Fixed the Lookup Tools window not appearing
 I was browsing some sites and found people asking how they can become hackers ...
I was browsing some sites and found people asking how they can become hackers ...
I loved that answer, I hope that the author be a solution for each Junior!![]() ........................................................................ Protection should learn first before they learn to hacker;
........................................................................ Protection should learn first before they learn to hacker;
The hacker must know the work of the following:
Should be allocated an area and is very much so it does best, such as programming languages (C++,php,vb...) and other;
And the use of search engine Google :)
But I recommend you do not use any program in the beginning Hak, whatever the circumstances;
And learn from the best of my Hack what you can;
At the stage of application and would advise you to freeze the body that it will freeze completely;
I know that the law of survival of the smartest hacker and you are always searching - as long as you use programs designed by others --
and i Have found a great article to see from here
Warning!
Do not forget that we learn to guard against hacker and not to sabotage is something we have on the animal thing as the mind ;)
>Special Security Team
A full explanation of the mask during navigation and protection of the tracking
Why you need to use proxy Diablo?
1. Transfer speed improvement. If the file you requested was received before to your proxy server, then proxy server will interrupt this file request and you will receive the file directly from proxy. However need to know, you can got the "speed down" effect. This effect appears when your proxy has long answer time because there is slow connection between you and your proxy server. 2. Security and privacy. Anonymous proxies destroys information about your computer in the requests header. So you can safely surf the net and your information will never be used by hackers and spammers. 3. Sometimes you encounter some problems while accessing to web server (for example, web-chat). You have mistaken while working with some data and / or the server administrator restricted access from your IP. So you can use the anonymous proxy and try to access again.
How to use proxy in Mozila firefox?
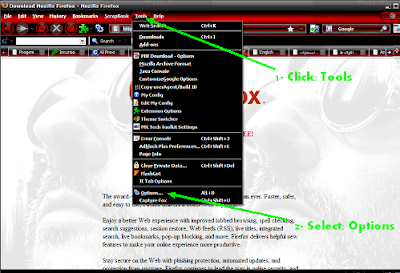




 End ! Press Ok Ok to exit
End ! Press Ok Ok to exit Working proxy list (anon. are shown with 10 min. delay)
| Proxy:Port | Latency | Type | Country | SSL | Uptime | Last work time |
| 72.18.206.166:8080 | 0.7540 | Anon. | US | ? | 11% | 2009-06-14 10:56:11 |
| 200.65.129.2:3128 | 1.5230 | Transp. | MX | Y | 100% | 2009-06-14 11:14:10 |
| 82.117.50.16:80 | 1.5250 | Transp. | NO | Y | 100% | 2009-06-14 11:14:10 |
| 88.191.94.176:3128 | 1.5720 | Transp. | FR | Y | 74% | 2009-06-14 11:14:10 |
| 69.30.227.98:3128 | 1.5920 | Transp. | US | Y | 78% | 2009-06-14 11:14:10 |
| 89.202.211.28:3128 | 1.6470 | Transp. | GB | Y | 96% | 2009-06-14 11:14:10 |
| 87.246.50.246:8080 | 1.6560 | Transp. | BG | Y | 63% | 2009-06-14 11:14:10 |
| 219.8.4.2:1080 | 1.6710 | Elite | JP | ? | 22% | 2009-06-14 10:53:11 |
| 200.65.127.161:3128 | 1.6760 | Transp. | MX | N | 100% | 2009-06-14 11:14:10 |
| 200.164.117.106:3128 | 1.6900 | Transp. | BR | Y | 100% | 2009-06-14 11:14:10 |
| 78.41.16.23:3128 | 1.6970 | Transp. | CZ | Y | 59% | 2009-06-14 11:14:10 |
| 77.70.86.54:808 | 1.7280 | Elite | BG | Y | 53% | 2009-06-14 10:53:11 |
| 65.42.208.146:8080 | 1.7570 | Transp. | US | Y | 60% | 2009-06-14 11:14:10 |
| 201.91.211.2:80 | 1.7810 | Transp. | BR | Y | 98% | 2009-06-14 11:14:10 |
| 200.30.101.109:8080 | 1.7950 | Transp. | CR | Y | 42% | 2009-06-14 11:14:10 |
| 201.53.100.127:3128 | 1.8060 | Transp. | BR | Y | 99% | 2009-06-14 11:14:10 |
| 189.21.192.74:8080 | 1.8110 | Transp. | BR | ? | 100% | 2009-06-14 11:14:10 |
| 200.223.225.129:8080 | 1.8240 | Transp. | BR | Y | 99% | 2009-06-14 11:14:10 |
| 200.196.242.143:3128 | 1.8360 | Transp. | BR | Y | 95% | 2009-06-14 11:14:10 |
GooD LucK !

Please add your comment !
>Special Security

The most secure and reliable to remove a computer virus. It works as follows: First you must select the boot from the CD drive in the bios (although most computers already with this option pre-installed). Place the CD in the drive, before loading the operating system. Option will appear to boot from CD / DVD, then you click a button to start the cd. Then, the CD will start! and then to load the files (this may take a little) the Eset Smart Securite will start. And then just run the scan. He is more English in its interface and easy understanding.
~~Download part1
~~Download part2
Protect Your PayPal Account from Hackers
Learn how to keep out hackers your PayPal account. With the ever growing popularity of PayPal, there are always people that want your money.
Protect Your PayPal Account by NEVER Opening Paypal Emails
One popular way that hackers are accessing PayPal is through email. Most people already know NOT to click a link in an email for their PayPal mail. Fake emails are supposed to be sent to spoof@ PayPal.com.
Do NOT ever open emails from PayPal. Do not open mails to see that a transaction occurred. Do not open mails that show you paid or anything. Everything that you need for financial record keeping for PayPal can be accessed directly from the PayPal site. You can print transaction logs directly from the PayPal site. You can print individual receipts from purchases and subscription payments directly from the site.
There is a hacker program that once you open an email, the program automatically retrieves your email password. Without your knowledge, the hacker sends a request to PayPal for lost password. PayPal then sends the new password information to the email. The hacker has your email password and can then automatically retrieve your PayPal password without your knowledge.
Keep the PayPal customer service number available. If an email has been received that the PayPal account has been compromised, it is best to talk to the customer service representatives instead of communicating via emails and on the PayPal site. Some emails state that the account has been compromised so that you will open that email. Once the email is opened it might be too late. These spoof emails are designed to create a panic and get you to click links inside the email. But the info that the hacker needs is given to them as soon as you open the email. Clicking the link just makes their job easier.
Protect Your PayPal Account by Calling Customer Service
If you open an email, call the PayPal customer service immediately. Tell them that your account was compromised. Ask for assistance on temporarily freezing the account until you can secure it again. Get the PayPal staff to help you secure your account.

Autorun Protector is a two way protection software that prevents your PC from infecting with autorun worms and also protecting your removable device from being infected from other sources. Hence, it decreases the spread of the worms. In addition, it also come with additional features like custom protected autorun.inf file, analysing/removing of autorun.inf & resolving drive opening issue. ~~Download
2-Additions must to the user at any browser Firefox(Cookies Sec)
Firebug integrates with Firefox to put a wealth of development tools at your fingertips while you browse. You can edit, debug, and monitor CSS, HTML, and JavaScript live in any web page... Firebug 1.4b1 requires Firefox 3.5b4 or higher.
~~Install
CAD Viewer 7.0.A.33 Network Edition

CAD Viewer 7.0 is designed to be easy to use for the non-CAD user, but CAD professionals will also appreciate features such as Back and Forward browsing, multiple file selection and batch printing. Supports all DXF and DWG versions to AutoCAD 2009 as well as HGPL and multiple raster formats.
Standard CAD Viewer 7.0 Features include:
• View and print all AutoCAD DXF and DWG drawings up to the latest AutoCAD 2009 NEW
• View PDF drawings NEW
• Save to PDF
• Browser style Forward/Back buttons allow multiple (up to 240) drawings to be loaded simultaneously.
• Intuitive User Interface
• Inquire Coordinates NEW
• Auto-orientation of print NEW
• Hold and Drag Pan method NEW
• Layers Control, including Named Layer States
• 3D pre-defined and user defined Views
• Can be called by other applications as a window for Viewing and/or Printing CAD drawings.
• Free upgrades for 12 months
• Enquire on Attributes attached to entities, Xdata supported.
• Read BMP, CAL, GIF, GP4, JPEG, PNG, TIFF raster formats.
• View ESRI shapefiles
• Read HPGL, HP-GL/2 (.PLT) plotter formats
• Read DWF (Drawing Web Format)
• TrueType fonts mapping
• 3D Shade / Render
• Can be used for 'slide show' presentations.
• Inquire on individual entities
• Thicken printed line widths
• High quality print output
• Print to Exact Scale
• Save to BMP, JPG, TIF, CAL, GIF, PNG
• Print single or multiple drawings via the command line with no limit on the number of drawings to print NEW (requires Batch Command license.)
• Reads Xrefs
• Paper Space / Model Space toggle
• Layouts support
• View, print, save, convert via the command line.
• Supports Viewports
• Multiple drawings selection via File Open or Windows Explorer
• Text Search
• Direct read of ZIP files
~~Download
VirtualBox 2.2.4
 InnoTek VirtualBox is a family of powerful x86 virtualization products for enterprise as well as home use. Targeted at server, desktop and embedded use, it is now the only professional-quality virtualization solution that is also Open Source Software.
InnoTek VirtualBox is a family of powerful x86 virtualization products for enterprise as well as home use. Targeted at server, desktop and embedded use, it is now the only professional-quality virtualization solution that is also Open Source Software.
Some of the features of VirtualBox are:
- Modularity. VirtualBox has an extremely modular design with well-defined internal programming interfaces and a client/server design. This makes it easy to control it from several interfaces at once: for example, you can start a virtual machine in a typical virtual machine GUI and then control that machine from the command line, or possibly remotely. VirtualBox also comes with a full Software Development Kit: even though it is Open Source Software, you don´t have to hack the source to write a new interface for VirtualBox.
- Virtual machine descriptions in XML. The configuration settings of virtual machines are stored entirely in XML and are independent of the local machines. Virtual machine definitions can therefore easily be ported to other computers.
- Guest Additions for Windows and Linux. VirtualBox has special software that can be installed inside Windows and Linux virtual machines to improve performance and make integration much more seamless. Among the features provided by these Guest Additions are mouse pointer integration and arbitrary screen solutions (e.g. by resizing the guest window).
~~Download
Microsoft Security Releases ISO Image - June 2009
 This DVD5 ISO image file contains the security updates for Windows released on Windows Update on June 9th, 2009. The image does not contain security updates for other Microsoft products. This DVD5 ISO image is intended for administrators that need to download multiple individual language versions of each security update and that do not use an automated solution such as Windows Server Update Services (WSUS). You can use this ISO image to download multiple updates in all languages at the same time.
This DVD5 ISO image file contains the security updates for Windows released on Windows Update on June 9th, 2009. The image does not contain security updates for other Microsoft products. This DVD5 ISO image is intended for administrators that need to download multiple individual language versions of each security update and that do not use an automated solution such as Windows Server Update Services (WSUS). You can use this ISO image to download multiple updates in all languages at the same time.
Important: Be sure to check the individual security bulletins at http://www.microsoft.com/technet/security prior to deployment of these updates to ensure that the files have not been updated at a later date.
This DVD5 image contains the following updates:
KB961501 / (MS09-022):
* Windows 2000 - 24 languages
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows Server 2003 for Itanium-based Systems - 4 languages
* Windows XP - 24 languages
* Windows XP x64 Edition - 2 languages
* Windows Vista - 36 languages
* Windows Vista for x64-based Systems - 36 languages
* Windows Server 2008 - 19 languages
* Windows Server 2008 x64 Edition - 19 languages
* Windows Server 2008 for Itanium-based Systems - 4 languages
KB968537 / (MS09-025):
* Windows 2000 - 24 languages
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows Server 2003 for Itanium-based Systems - 4 languages
* Windows XP - 24 languages
* Windows XP x64 Edition - 2 languages
* Windows Vista - 36 languages
* Windows Vista for x64-based Systems - 36 languages
* Windows Server 2008 - 19 languages
* Windows Server 2008 x64 Edition - 19 languages
* Windows Server 2008 for Itanium-based Systems - 4 languages
KB970238 / (MS09-026):
* Windows 2000 - 24 languages
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows Server 2003 for Itanium-based Systems - 4 languages
* Windows XP - 24 languages
* Windows XP x64 Edition - 2 languages
* Windows Vista - 36 languages
* Windows Vista for x64-based Systems - 36 languages
* Windows Server 2008 - 19 languages
* Windows Server 2008 x64 Edition - 19 languages
* Windows Server 2008 for Itanium-based Systems - 4 languages
KB970437 / (MS09-018):
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows XP - 24 languages
* Windows XP x64 Edition - 2 languages
KB969805 / (MS09-018):
* Windows 2000 - 24 languages
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows Server 2003 for Itanium-based Systems - 4 languages
KB963093 / (MS09-023):
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows XP - 24 languages
* Windows XP x64 Edition - 2 languages
KB970483 / (MS09-020):
* Windows 2000 - 24 languages
* Windows Server 2003 - 18 languages
* Windows Server 2003 x64 Edition - 11 languages
* Windows Server 2003 for Itanium-based Systems - 4 languages
* Windows XP - 24 languages
* Windows XP x64 Edition - 2 languages
~~Download
 IObit Security 360 is an advanced malware and spyware removal utility that detects, removes and protects your PC from various of potential spyware, adware, trojans, keyloggers, bots, worms, and hijackers.
IObit Security 360 is an advanced malware and spyware removal utility that detects, removes and protects your PC from various of potential spyware, adware, trojans, keyloggers, bots, worms, and hijackers.
With the unique "Dual-Core" engine and the heuristic malware detection, IObit Security 360 detects the most complex and deepest spyware and malware in a very fast and efficient way.
IObit Security 360 has a real-time malware protection and frequent automatic updating for prevention of zero-day security threats. IObit Security 360 can work with your Antivirus for a superior PC security.
Features:
* Complete PC Security Care
* 1-click Solution and Very Easy to Use
* Very Fast and Light
* Finds the Deepest Infections
* Automatic and Frequent Updates
* Work with All Antivirus Products
* Free for Home/Non-commercial Use
~~Download
Loaris Trojan Remover 1.1.6.8
These programs have the ability to track your browsing habits and even steal such personal information as bank account numbers and passwords. Spyware has the power to install more parasites on your computer without your consent. Everything you do and everything you type is being recorded right now! Companies know what your interests are! Hackers will access your PC and do anything they wish. They can even steal your Identity and You would never be the wiser! The Solution: Download the latest version of Loaris Trojan Remover right now. You will be able to completely clean your computer of all these invasive threats! Your computer will be clean and will run alot faster - Your Privacy will be Protected! Rar pass:S-sec.BlogSpoT.coM
Are you bombarded with popup ads, seeing new toolbars in your browser, is your home page changing to unwanted destinations or are you bombarded with irritating spam? Perhaps strange software loads on startup or your favorites have new entries that YOU DONT WANT. If So.. Your PC is most likely infected with adware, spyware, spybot, trojans or another internet parasite.
ProxyShell Hide IP 3.0.1

ProxyShell Hide IP is a powerful proxy software to hide IP address when you surfing by intelligently managing and using multiple proxies, makes you surf anonymously, protects your personal information and internet privacy. With ProxyShell Hide IP, you can hide IP address, surf the web without anyone knowing who you are, hide your own information and reading interests. ProxyShell Hide IP could also bypass restrictions if your IP address is blocked, post on bbs or send email without displaying your own IP.
Key Features
• Hide IP address to make you surf anonymously
• Unique algorithm to effectively use public proxy servers for surfing
• Use multiple proxies simultaneously to handle your surfing requests
• Intelligently optimize speed of multiple proxies, accelerate your surfing
• Automatically detect proxy errors and change proxies if necessary
• Totally automatic and easy-to-use
Creating Games in C++: A Step-by-Step Guide

Do you love video games? Ever wondered if you could create one of your own, with all the bells and whistles? It’s not as complicated as you’d think, and you don’t need to be a math whiz or a programming genius to do it. In fact, everything you need to create your first game, “Invasion of the Slugwroths,” is included in this book and CD-ROM.
Author David Conger starts at square one, introducing the tools of the trade and all the basic concepts for getting started programming with C++, the language that powers most current commercial games. Plus, he’s put a wealth of top-notch (and free) tools on the CD-ROM, including the Dev-C++ compiler, linker, and debugger–and his own LlamaWorks2D game engine. Step-by-step instructions and ample illustrations take you through game program structure, integrating sound and music into games, floating-point math, C++ arrays, and much more. Using the sample programs and the source code to run them, you can follow along as you learn.
Bio: David Conger has been programming professionally for over 23 years. Along with countless custom business applications, he has written several PC and online games. Conger also worked on graphics firmware for military aircraft, and taught computer science at the university level for four years. Conger has written numerous books on C, C++, and other computer-related topics. He lives in western Washington State and has also published a collection of Indian folk tales.
~~Download











![[2a6jvpg.jpg.gif]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh3DeVwIT-rEycs4ctNT_UgpN21U1q3RdP9EXdVwqjokQY4NqnNBpYGQiHOjnWQmglOPKSDXY6-kcRpma2OHgAGCcZc7kWrO1NJ_P2oNHWWiuVXxaWw9f9idyRfLbvfdpxZ5xb3hKMl6nnS/s1600/2a6jvpg.jpg.gif)
![[Specialsecurity.gif]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiHdW_yAzCMaTqyzMc0_GRFdQ2xE-zzIl8mKdce4euar70R1CDH8hMM17hcOv5KWTrHQdt7CCPpbTzOPQAahU72e-UmyHSii9pkIOZV0ETPdrnKo21UgGYExqIqkuBgWNMZ7YEX47bSUCKa/s1600/Specialsecurity.gif)














