PC Security: The Ultimate Guide.
The Ultimate Guide to PC Security
Being a hacker, you're coming face to face with some of the most malicious programs on the internet every day. You want to be secure. Most of the programs you'll be downloading will be malicious, so how can you tell if the program will be working against you or for you?
This guide will be looking at the scanning of malicious files, as well as a guide to anti-viruses & firewalls and a brief introduction to sandboxing and anonymity. So yep, you're in for quite a bit of reading. Grab a drink, maybe a cigarette.
Being secure is important. Just because you call yourself a hacker, it doesn't mean you're immune to attacks towards your computer. Without my anti-virus, I doubt I'd actually be typing this now - I'd probably be searching through my registries and screaming like a chicken on speed. I'm like that.
Not all anti-viruses work the same way. Some anti-virus programs are bad; some are good, and some are just plain useless. We'll be looking at which ones are the best of the best, and which ones are just plain fail.
Being infected with something can also put your friends and family at risk, other users of your computer could be having their login & credit card details stolen without any knowledge of it. Worms can also spread to your email contacts and friends on popular websites such as Facebook.
Downloads & Scanning
For example, you download a program and the poster is claiming that it is a clean botnet controller. If we can this, it will come up with results such as "Win32/RBot" etc.. This means that the file should be what we wanted.
Now, if the botnet-controller scan came up as something like "Win32/trojan.agent.a", we can tell that this is a malicious program that will work against us. This is an example of a download you do not want to use.
All in all, the scan should show results similar to what you were downloading.
You should always be careful what you download. You may often be downloading malicious software without even realizing sometimes. Trust me, this happens to a lot more people than you think.
If you're expecting a file to be much bigger than the download you find, don't touch it. An example of this would be "Windows XP Theme - 350kb!" when it should be a lot higher, such as 30-50mb.
Remember to always check the names of the files you download.. If you're downloading a cracked program, it would be unusual for it to have no credits or advertisements in it. I would trust " 'x' cracked by 'y' " more than I'd trust " 'x' crack". Credits, names or advertisements should nearly always be in .rar or .zip files, this is one good way of recognizing a trusted download.
Here is a quote from Wikipedia which you may find helpful: "Example: ZTreeWin_1.5.zip contains a crack to register ZtreeWin 1.51 included files are: keygen.exe, one.nfo, file_id.diz and 'RUN.EXE'. It is the 'RUN.EXE' that contains the rogue program". Downloading really isn't necessary and is often risky.
Online File Scanners
Web-scanners such as "VirusTotal" and "NoVirusThanks" are becoming increasingly popular with the amount of anonymous downloads posted all over the internet.
If you want to scan a file you find suspicious, you can go to either VirusTotal - Free Online Virus and Malware Scan or NoVirusThanks.org - Home to do so.
VirusTotal will send samples of the file to the antivirus companies, so this is not recommended if you want to keep your file undetectable.
NoVirusThanks has an "Advanced options" area where you can choose to not distribute your file to the antivirus companies, this is handy for keeping things fully undetectable, but if it's a file you don't trust and don't want yourself or others to be infected by it in the future, I suggest you allow them to distribute it to the antivirus companies. I respect what these websites and the malware fighting websites do, and so should you.
Visiting Websites & Reading Emails.
Be cautious of the websites you visit. I wouldn't recommend visiting any websites that seem cheap, uncommon, or freely hosted. Malicious websites are often misleading or can just inject things into your system without your consent. If you use the "Chrome" browser from Google, you may have noticed that it automatically downloads files without prompting you. Chrome is a browser I would not recommend just because it is so new, all new things have vulnerabilities, and if a vulnerability can be exploited, it will be exploited.
I'm behind a firewall and anti-virus anyway, but the only websites I visit are popular ones. The untrustworthy and uncommon websites usually don't appeal to me, for obvious reasons..
When opening emails, you should also be cautious. Just because it's an email from your friend - it doesn't mean you can trust it! You may see some emails asking you to update your bank details -- your banks should never ask you to do that via email. The details you enter will be sent out to someone who is going to exploit your details, so steer away from these emails.
Worms can be spread via email. For example, you open an email from Bob containing a worm, this worm is then sent to all of your contacts. This is how most worms will work, and it is suggested that you change your emailing service if it could be vulnerable. You can use Microsoft's live hotmail service which is excellent, it will also disable any harmful content from downloading onto your computer. You can find this service at Sign In
Sandboxing
By using a sandbox, everything that is downloaded onto your computer will remain in the sandbox. It will not escape, meaning that malicious downloads cannot harm your computer. Sandboxing is a great way to test whether or not a website can be trusted. I rarely do this, but it's so useful sometimes.
Sandboxing will also protect your cookies, history and cached temporary files from being leaked. Downloads are isolated, meaning that they are trapped and your computer is protected.
Here is a download I have for Sandboxie v3.30: RapidShare: Easy Filehosting
Firewalls
The good antiviruses will have a built-in Firewall, but if not, then it may be worth downloading one. Firewalls aren't essential, but can help a lot.
Some firewalls have IP masking options, but these can usually slow down your computer and are not worth using unless you're doing something illegal.
The main use of a firewall is to prevent incoming traffic, which will stop things like 'telnet' from reaching your connection, and can also stop worms etc. from accessing your network. Firewalls will also block the backdoors that trojans create, so if you find yourself unlucky enough to have a RAT (Remote Access Trojan) on your computer, the backdoor should be blocked by your firewall, but it is possible for a trojan to bypass this. Having a firewall does not mean you are secure, many firewalls can be easily disabled or bypassed by malware. Some firewalls will also block legit connections, such as downloads for software. Do not think you're secure just because you have a firewall, this is a common misconception with firewalls. Too many people think that by installing a highly popular firewall, they'll instantly be secure against the latest intrusions, but this is not at all true.
Firewalls may also make an effect on your connection speed. If you have a very fast download speed, you may notice a difference when you get a firewall, but the download speed may remain normal on users with slower speeds. This effect can vary between users, and depends on the connection. It's best to try several firewalls to find out which one suits you best - reviews are personal and will not always be the same for everyone.
One of the favourite firewalls is "ZoneAlarm" which is very popular and has a free version. The paid version is obviously better, but it isn't necessary at all.
If you're using Windows Vista, I'd recommend choosing ZoneAlarm as your firewall. The same goes for XP, but you might want to get your hands on a "BlackIce" crack instead, if possible.
Another great Firewall is "Comodo" which is also free can be found here...
Comodo: Free Firewall Software Download by Comodo
Zone Alarm: ZoneAlarm by Check Point - Award winning PC Protection, Antivirus, Firewall, Anti-Spyware, Identity Protection, and much more.
Ghost: GhostWall FireWall
Antiviruses
An anti-virus program is essential. You honestly shouldn't go without one. If you don't have one, there is a list of downloads and recommendations in the next post. Don't be worried about the anti-virus slowing down your computer, if you get the right one then your computer will remain at maximum performance.
You want an antivirus that will scan your RAM and system folders constantly, because then you will be alerted if something harmful has been found in them. The average antivirus will only scan and remove when told to, but the best ones will scan constantly, update daily, and give plenty of tweaking options to fit to your preferences.
If there are malicious programs that you want to download such as Metasploit, it is best if you have an antivirus that will allow you to do so. Some antivirus programs will give you no option and will quarantine the file straight away, but others such as Kaspersky will give you the option to clean, remove or ignore.
Viruses can sometimes fully disable your protection, but the stronger programs such as Nod32 can withstand this and will be unclosable. You want something tough if you're going to be downloading riskware.
A good anti-virus will also constantly scan your downloads and running processes. Hopefully you are able to understand now why these are essential.
If you want to run more than one antivirus, you must find a combination that works. If you have a good antivirus, you won't need to. Infact, you shouldn't ever need to run more than one. I remember having Kaspersky running while I installed Nod32, my PC growled. :3 The only antivirus-related programs I have installed at the moment are HijackThis, ComboFix and NOD32. I like to use HijackThis to see what's running on my computer, and I always keep ComboFix just incase, you never know what's round the corner...
I remember having no antivirus software installed whatsoever, and then I received a rootkit that wouldn't let me download any software.. I got rid of them eventually, but it wasn't easy, the rootkit wasn't detected by most AV's because of it being so new/rare - you still can't find it on a few of the AV databases! But I do wish I had it again, so I could send it out as a sample.
I will be listing my favourite anti-viruses in the next part. I strongly recommend you stick to these, as there are many fake ones that you can be easily lead to. Remember to look things up before downloading them. Pick wisely! :3
The Top 5 Anti-virus Programs.
Here's the list of my top five favourite anti-virus programs in order.
You can pick which you want from each picture, but I'd recommend Kaspersky.
Kaspersky:
Download - RapidShare: Easy Filehosting
Password - a4f1exsid1ec

Nod32:
Crack (Doesn't get updated) - RapidShare: Easy Filehosting
Logins for legit version -
Username:EAV-07473176
Password:a2esnt85nh
For more, try nod32??-??nod32??id?nod32??????nod32??
(Legit version available at Antivirus and Antispyware Software - Download ESET NOD32 Antivirus or ESET Smart Security and eliminate viruses)

Avast:
Avast also has skins available, which is great!
Free download: Download FREE antivirus software - avast! Home Edition

Bitdefender:
Free downloads: Free Anti Virus Downloads - BitDefender

AVG:
Credits to Goodkidz for the download.
Download: RapidShare: Easy Filehosting

Essential Additions.
There's a few more tools which I'm sure you'll definetely want to get.
HijackThis is a tool used to scan the areas of your computer which viruses are often located in. It will also scan the registry areas which hold the legitimate programs and, quite often, the infections. It is best not to delete ('fix checked') any entries on HijackThis unless you know what you're doing, as you may be removing something which is a required part of your system.
Another good thing about HijackThis is the fact that it's so lightweight, it uses barely any memory, it's easy to use, and you don't need to keep it running!
This is a great area to check if a process is harmful or not: Startup Programs Database
HijackThis can be found here: TrendSecure | TrendMicro HijackThis Overview
Browser Protection
There are several great addons for browsers which you can get to protect you from malicious websites.
If you use FireFox, look for "WOT" and "NoScript", WOT will give warnings before you visit a website, and NoScript will disable malicious scripts from running when you visit a website.
If you use Internet Explorer, look for "IE-Spyad", IE-Spyad will redirect you away from malicious webpages and guard you from over 5,000 different URL's.
I'm also working on my own plugin, which you can expect to see in a few months. This will be for IE only, until I fully figure out how FireFox operates.
Okay, now that you're protected (well, I hope you are), it's time to be invisible...
IP Hiders
You can get some great IP hiders to keep you anonymous.
A personal favourite is "Hide-The-IP", which allows you to select the proxy and choose the speed of the one you want.
Hide-The-IP can be found here: Hide The IP - Hide IP Anonymous Surfing Software - Though you may need to find a crack for it!
There are many fabulous IP hiders out there which can be found, and these are a must if you're going to be involved in any illegal activity.
Tor: Anonymity Online
You may want to download "Tor" and TorButton for FireFox. This is a program which will select a proxy for you and allow you to spoof your connection by using that.
TorButton is a FireFox addon which allows you to change your proxy quickly by clicking the button. This is a great tool, and another good reason to download FireFox!
The whole Tor website with information & downloads can be found here: Tor: anonymity online
Alright, grab another cup o' coffee, 'cause we've still got more to do..
Personal Details
Okay, you may want to give out your name and things on your Facebook or MySpace, but if you do, it's wise to use an alternate alias. If someone searched your hacking alias in Google, they'd probably be able to pick up a lot of information on you from that. Think about the name you choose before you choose it, and make sure you don't over-use it - only use it where you think you should. Don't complain about not being anonymous if you're going to splurt out your details everywhere, you can't expect to stay hidden if you're going to give yourself away without realising. Remember that.
Keeping Software Updated
Software should always be kept updated. This is vital. Most security experts will tell you that updating your software is more important than having an antivirus, because malware finds flaws and vulnerabilities in software that it can exploit.
This is what should always be kept fully up to date:
Your operating system (e.g. updating from Windows XP SP1 to SP2).
Java.
Browser.
Antivirus.
Firewall.
Instant messaging or email applications.
Any other software which could be exploited.
Zer0man showed me this lovely website with scanners you can use to check for out-of-date software...
Here's the online version: Scan Now - Online (OSI) - Vulnerability Scanning - Secunia.com
And the downloadable version: Download - Personal (PSI) - Vulnerability Scanning - Secunia.com
Quite obviously, the downloadable version scans for more vulnerabilities than the online version, and it includes more features. This is a great tool to use every few weeks, since you never know what's around the corner ;-)
Active Thinking
Many scams and computer infections require your consent, so you should always be wary. If something doesn't quite look right, make sure to research it. Many people are fooled into giving away their details by fake emails from companies such as banks, social networking websites, etc. You shouldn't believe everything you read. Many scams will lead you on, so you just have to watch out. Keep everything you've learned from this guide in mind, and you'll be safe.
A good quote from The Real Hustle: "If it looks too good to be true, then it probably is".
Passwords
Though it is also important to have a password you will remember, you should also be sure that it can't be guessed. If it's a site containing personal information, I suggest you change your password once a month. A good password would contain letters, numbers and symbols - maybe even words in a foreign language if it helps! An example of a good password would be "A$fao4iz3£p" not "John1982" or "ilovefootball". Passwords should be different for each website you use, because if someone hacked into a forum, for example, and took your details - potentially, they could have access to your PayPal account, Facebook, etc.
Well, you should know just about everything you need to know by now. If there's anything else you're wondering, don't hesitate to ask! I will be here for any questions, feedback or suggestions. This guide should keep you well-hidden and protected from now on, just remember to keep everything in mind!
Originally written for another website,
re-edited for S-Sec.Blogspot.COm & InterN0T.Net
Manually Removing Computer Viruses
Process Explorer
HiJack This
Malware Bytes Anti Malware
Quick Guide
For anyone in a hurry, read this paragraph. Removing a computer virus is a time consuming task. Nobody ever has just one single virus, and having a virus is like having an ant in your house, it usually returns with an army. A virus scanner is a good deterrent, but if the product is out of date then its a useless product. Tracking down a virus is a matter of knowing what processes on the computer are running, and what should not be running. Any process with a suspicious sounding name or one that's consuming much system resources could be an indication of something more malevolent. Tools to help are system config, task manager and autoruns. When finding a suspect process, look it up on google. If it does turn out to be a virus or malware then sometimes killing the process will work. You also have to find where its called from, and either delete the offending keys in the registry, start service or start-up program. Malware bytes file assassin, or the malignant file remover from the linux side of the disk can take care of locked files. Once all threats have been removed its a matter of rebooting and checking the computer, usually you're looking at 2 hours work, and sometimes if things are really bad you have to decide its its cheaper to wipe the hard drive and reload windows.
Virus Definitions
In its simplest term, a computer virus is a file that can copy itself. This doesn't sound too bad but its the "payload" that the virus can carry that makes it a real security threat. Some viruses are designed to delete files, others can steal passwords, some are designed to make your computer unbootable. There are other types of viruses, defined in simple terms:-
Virus - a file that can copy itself
Trojan - a program that contains a virus or malware
Spyware - a file or program designed to intercept or take partial control of a computer
Malware - a program designed to damage a computer without the owners consent
Worm - a network travelling virus
All the above can loosely be called viruses, and keeping a computer protected is a constant battle between good and evil. The best way is to run an anti virus program and keep it updated. An outdated product is a useless product.
Virus Removal
If you suspect a virus, then the first step is to run a virus scan from windows. You may get lucky and the anti virus (AV) program detects and can remove the virus. If the AV program can detect the name of the virus but cannot remove it, make a note of its name and research it on google. There may be a downloadable utility that can do this for you.
If no Virus is Detected
If an anti virus scan and spyware scan have revealed nothing, and the computer is still running slow or behaving oddly, you'll need to check what processes are running. The next section should help and special tools are available in the form of task manager, autoruns, process explorer and hijackthis.
Displaying Processes
At any time windows always has many running processes. A process is an individual task that the computer runs. In general, the more processes, the more work the computer has to do and the slower it will run. However its not just the number of running processes, whats also important is the amount of system memory (RAM), hard drive space and processing speed. These are known as system resources and every process affects the system resources. Each task is given a process number or PID. Process ID's start at 1 and are assigned by the system kernel. The system kernel is the core of the operating system, but unlike other operating systems e.g. linux, the windows user has no control over the running kernel, but can see its performance via task manager and other tools. The easiest way to see how a system is running is by using Task Manager. Task manager can be started from right clicking the taskbar or pressing Ctrl-Alt-Delete , screenshot below:

Task Manager
The screenshot above is taken from my own computer running Windows XP. For comparison I will also run autoruns and hijack this on the same system.
The screenshot above has more information than a the standard task manager. To view the extra columns, press View, then Select Columns, tick boxes for VM size, Handles, Threads , I/O Read Bytes and I/O Write bytes and you should have a similar display. The bottom line shows 24 processes and CPU usage as 0%. If the computer appears sluggish and takes forever to do anything, you may see a high number of running processes and CPU usage of 100%. CPU usage only drops to 0% when the system is idle, at any other time the running figure will be between these limits; the lower the usage the faster and more responsive the system will be. A quick explanation of the columns:-
Image Name the name of the current process or task.
PID the Process ID number of the current task
User Name the name of the owner of the task
CPU amount of CPU usage in percent
Mem Usage amount of physical RAM used by the task
VM Size amount of Virtual Memory allocated to task
Handles number of open files that the process is using
Threads amount of other simultaneous tasks running in association with current task
I/O Read Bytes amount of information that the process is reading from disk
I/O Write Bytes amount of information that the process is writing to disk
Task Manager Performance Window
Clicking the performance tab will produce a useful display, see below.

The top right shows overall CPU load, at idle it will be 0%, full load 100%. To find out what process is using the CPU click the processes tab and then the CPU column to arrange in CPU load order. To the right is CPU usuage history, bottom left shows the amount of memory used in the Paging File (PF). The paging file (see virtual memory) is very important. On computers with modest and low amounts of memory, any labour intensive task will read and write information to and from the paging file. As the paging file is created on a hard disk, which is thousands of times slower than physical memory the computer will run slow. Physical memory is shown in KB at the lower right of screen. If the value of the PF, is greater than the physical memory, then the computer would benefit from more RAM, or require a tuneup to remove superfluous programs.
Using Task Manager Information
Suppose now you come across a computer and its hard drive is constantly thrashing. Bring up task manager turn on I/O read and write bytes. Click on the I/O bytes read column and it is sorted in order of disk usage; you can easily see what process is hammering the hard drive. Suppose the computer is very slow, then by clicking on the CPU usage column, you should be able to see which process is hogging the CPU.
Virtual Memory
All computers require physical memory (RAM) to run their applications. Once all available RAM has been used, memory is supplemented by reading and writing to a file to the hard drive. This file is called the Paging File and acts as virtual memory (although hard disk are a thousand times slower than memory). On machines with 256M of memory or less (or any computer attempting to run many programs) the system RAM soon gets used and the paging file gets created. When this happens the end user will notice a big drop in performance. Again you can see which tasks are the heavy users of VM by highlighting the VM column in task manager. This is one reason why Norton Antivirus should not be run on a computer with less than 256M RAM, its massive amounts of resources leave little memory for any other task and you're constantly waiting for the hard drive to read and write from the paging file.
Checking Running Processes
If a customer reports a problem with a computer, the first place to look is task manager. You need to know what's running and should it be running?. This is where skill is required. With practice you can quickly identify system and user tasks, network processes and services. Anything unknown you look up on the internet. It soon becomes clear what's normal and what tasks could possibly be viruses or malware.
Some handy resources to help on the Internet are:
McAfee Threat Library
Start up Programs
Task List Org
Knowing whats running and what looks suspicious takes experience and a trained eye. Some virus writers now deliberately use process names that look similar to real tasks e.g. taskmgr.exe (the real task manager process) and taskmgr.exe which is an email worm.
Killing Processes
In task manager this is as easy as highlighting the process, right clicking and choose kill process. (See screenshot).

Some processes will terminate instantly, others may cause a system crash and others may give a locked file warning.
Dealing with Locked Files
If a file is in use you will get an access denied message or similar. To delete locked files, you can seek out all threads and file handles (very time consuming) or use Malware Bytes File Assassin Tool, part of the malware bytes anti malware program (ans also on the CD in the tools folder). This automatically deletes all file handles and kills the file on reboot. An alternative is to run the CD in linux mode and use the Malignant File Removal Tool.
Finding Running Processes
System Tray
A quick word about the windows system tray. This is usually at the bottom right of the taskbar but can be moved about. The system tray from my computer is shown below:

Every item starting in the system tray will create 1 or more additional processes, the more items starting in the system tray, then the slower the system will start. If a user installs software with default choices then many items will be shown here. Its not necessary to have anything in the system tray though for convenience most people like the volume control and clock.
System Configuration Utility
The easy way to find out where processes are started from is the system configuration utility, image below. Start this from the run dialog box by typing msconfig, or control panel. There are several tabs, the startup tab is shown below:

Unticking the box disables the start process, but does not delete it. This is a safe way to carry out diagnostics, as if needed, ticking the box enables the process again. Similarly startup services can be disabled as can entries in the win.ini file. Do not be tempted to experiment here, disabling a needed service can render the computer unbootable.
Services
Bringing up the services list from either computer management, typing services.msc in the run dialog box or services in the find utility in Vista will appear similar as below.

A service is what the operating system controls, and can be set to automatic, manual or disabled. Stopping some services will prevent windows from running, but some malware and virus writers now attempt to evade discovery by creating an entry in the services list.
A comprehensive list of services and description can be found on Wikipedia, click here.
AutoRuns
A much more powerful version of task manager, available as freeware is Autoruns, screenshot below. Autoruns combines all the features of task manager, msconfig and the services list as a powerful all-in-one diagnostic and configuration utility.

At first look this is a mine of information, and working with this program takes a few hours practice. The snapshot above is taken from my own computer, and has the same running processes as task manager. In the everything tab, the fourth heading which starts:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
contains many of the user started processes. Unlike task manager, a description is given and also the image path to where the program is started from. In the screenshot AVG is the anti virus, two drivers are running for an Nvidia graphics card, and Clone Cd tray is a user choice program. System services are displayed under the system tab, whereas in task manager they are all lumped together.
To prevent program from loading untick the tickbox at the extreme left. The entry can be right clicked and deleted, but after making any changes, a reboot is first advised and check for system stability.
Process Explorer
An extension of Autoruns is the partnering program Process Explorer, shown below.

Any item from autoruns, can be right clicked and opened in process explorer. As with task manager, disk I/O, virtual memory and memory usage can also be viewed. Clicking any columns allows the display to be re-arranged in order of the highest system resource. A useful feature is the command line path and a right click allows individual resource management of a process to be graphed.
Hijack This
The next diagnostic tool in the tools folder is known as Hijack This, screenshot below:

Hijack this is very powerful tool and a cross between Task Manager and Autoruns. From the main menu of hijack this a system scan takes a snapshot of all running processes and system services. In addition it includes many more entries, not shown in task manager, but present in autoruns. Each item has a category that can be look up using the info button. I'm going to explain some of the more notable entries:
R0,R1,R2,R3 - Start page and search page for Internet Explorer. If any entry looks suspect and you see a URL that looks suspicious (not the customers start page) uncheck the box and click Fix Checked button.
F0,F1,F2,F3 - Autoloading Entries from old INI files. These are old autoloading entries from older windows versions. F0 references are always bad, F1 to F3 are usually old programs, research on google if unsure.
01 - Hosts file redirection. The windows hosts file has been intercepted and possibly used in a browser redirect. To correct edit the file or untick the entries..
04 - Autoloading Programs from Registry or Startup Group. Any program that loads automatically will be referenced here. This includes legitimate driver files and programs of the users choice. This is also where many spyware and malware programs start. Killing them here will stop them from reloading. Tread carefully and be warned, there is no way to put an item back in place, should you make a mistake.
23 - Startup services. These are just the running services, making it easier to see what service has started. The service tab in windows computer management lists all services, whether running or not.
These are the main categories, information on any other item can be found from the main tool bar and clicking on info. TrendSecure have also provided some information about Hijack This in the form of their Quick Start Guide.
Final words of advice, with thousands of viruses, malware and spyware on the loose at any time, its an impossible task learning everything and keeping up to date. The best advice is to use the links and "Google" at all times. It takes many years to become an expert.
Malware Bytes
Anti virus programs look for files that have been corrupted with a known virus signiture, anti spyware programs will look for files or registry entries that are known spyware. However malware may often exist and lay undetected. Malware is a program or utility, often disguised as something familiar, perhaps an anti virus program, but instead does not do what it claims to be, and instead will hijack your browser, delete files or other damage to your computer. Malware Bytes offer a free utility called Malware Bytes anti malware, screenshot below:

Running a scan with Malware Bytes Anti Malware may save you hours of work, there is an update tab to update the latest malware definitions, and if malware is detected the program offers to reove it for you.
source:Media Section
Learn What is Phishing and save your money from Hackers

Phishing is an attempt to criminally and fraudulently acquire sensitive information, such as usernames, passwords and credit card details, by appearing as a trustworthy entity in an electronic communication. eBay, PayPal and other online banks are common targets. Phishing is typically carried out by email or instant messaging and often directs users to enter details at a website, although phone contact has also been used. Phishing is an example of social engineering techniques used to fool users.Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical measures.
Recent phishing attempts have targeted the customers of banks and online payment services.Social networking sites such as Orkut are also a target of phishing.
Spoofed/Fraudulent e-mails are the most widely used tools to carry out the phishing attack.In most cases we get a fake e-mail that appears to have come from a Trusted Website . Here the hacker may request us to verify username & password by replaying to a given email address.
TECHNIQUES BEHIND PHISHING ATTACK
1.Link Manipulation
Most methods of phishing use some form of technical deception designed to make a link in an email appear to belong to some trusted organization or spoofed organization. Misspelled URLs or the use of subdomains are common tricks used by phishers, such as this example URL
www.micosoft.com
www.mircosoft.com
www.verify-microsoft.com
Instead of http://www.microsoft.com/
2.Filter Evasion
Phishers have used images instead of text to make it harder for anti-phishing filters to detect text commonly used in phishing emails.This is the reason Gmail or Yahoo will disable the images by default for incoming mails.
How does a phishing attack/scam look like?
As scam artists become more sophisticated, so do their phishing e-mail messages and pop-up windows.They often include official-looking logos from real organizations and other identifying information taken directly from legitimate Web sites.Here is an example of how the phishing scam email looks like

Example of a phishing e-mail message, including a deceptive URL address linking to a scam Web site.
To make these phishing e-mail messages look even more legitimate, the scam artists may place a link in them that appears to go to the legitimate Web site (1), but it actually takes you to a phishing site (2) or possibly a pop-up window that looks exactly like the official site.
These copycat sites are also called “spoofed” Web sites. Once you’re at one of these spoofed sites, you may send personal information to the hackers.
How to identify a fraudulent e-mail?
Here are a few phrases to look for if you think an e-mail message is a phishing scam.
“Verify your account.”
Legitimate sites will never ask you to send passwords, login names, Social Security numbers, or any other personal information through e-mail.
“If you don’t respond within 48 hours, your account will be closed.”
These messages convey a sense of urgency so that you’ll respond immediately without thinking.
“Dear Valued Customer.”
Phishing e-mail messages are usually sent out in bulk and often do not contain your first or last name.
“Click the link below to gain access to your account.”
HTML-formatted messages can contain links or forms that you can fill out just as you’d fill out a form on a Web site. The links that you are urged to click may contain all or part of a real company’s name and are usually “masked,” meaning that the link you see does not take you to that address but somewhere different, usually a scam Web site.
Notice in the following example that resting the mouse pointer on the link reveals the real Web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company’s Web address, which is a suspicious sign.

So the Bottom line to defend from phishing attack is-
1.Never assume that an email is valid based on the sender’s email address.
2.A trusted bank/organization such as paypal will never ask you for your full name and password in a PayPal email.
3.An email from trusted organization will never contain attachments or software.
4.Clicking on a link in an email is the most insecure way to get to your account.
By:sukak2r2
Installing VMWare Workstation 6.5.2 On BackTrack 4
As usual, brand new kernel woes with VMware. Here’s a quick way to patch up VMware 6.5.2 to get the modules to compile. Start by downloading and installing VMWare Workstation 6.5.2.

Once that’s done, run the following commands:
rmmod kvm_intel kvm
echo blacklist kvm >> /etc/modprobe.d/blacklist
cd /tmp
wget www.offensive-security.com/tools/bt4-vmware-workstation-patch.tar.bz2
tar jxpf bt4-vmware-workstation-patch.tar.bz2
chmod 755 vmware-6.5.2-modules-2.6.29-fix*
./vmware-6.5.2-modules-2.6.29-fix.sh
vmware-modconfig –console –install-all
vmware
Done!
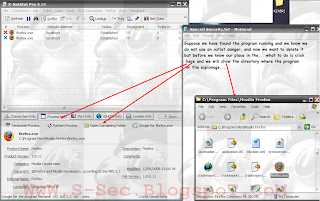
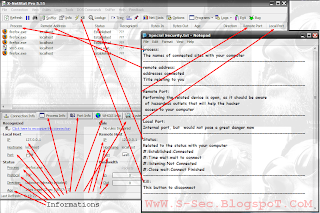
Source: Offensive SecurityKnowledge of open access with port and protection from penetration
| X-NetStat Professional Program Features: | |
|
|
Rar Pass:S-sec.BlogSpoT.coM
+ Added Google search buttons next to remote IP and hostname
+ Added -stealth command line parameter to run the program completely hidden.
+ Added -shutdown command line parameter to shut down the program.
+ Fixed the Lookup Tools window not appearing
A full explanation of the mask during navigation and protection of the tracking
Why you need to use proxy Diablo?
1. Transfer speed improvement. If the file you requested was received before to your proxy server, then proxy server will interrupt this file request and you will receive the file directly from proxy. However need to know, you can got the "speed down" effect. This effect appears when your proxy has long answer time because there is slow connection between you and your proxy server. 2. Security and privacy. Anonymous proxies destroys information about your computer in the requests header. So you can safely surf the net and your information will never be used by hackers and spammers. 3. Sometimes you encounter some problems while accessing to web server (for example, web-chat). You have mistaken while working with some data and / or the server administrator restricted access from your IP. So you can use the anonymous proxy and try to access again.
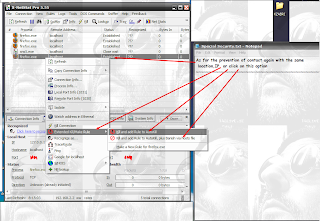
How to use proxy in Mozila firefox?
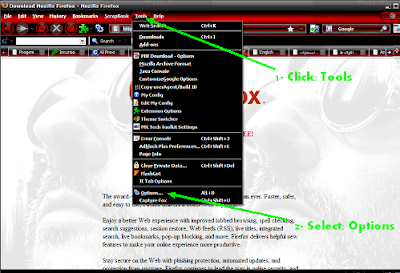




 End ! Press Ok Ok to exit
End ! Press Ok Ok to exit Working proxy list (anon. are shown with 10 min. delay)
| Proxy:Port | Latency | Type | Country | SSL | Uptime | Last work time |
| 72.18.206.166:8080 | 0.7540 | Anon. | US | ? | 11% | 2009-06-14 10:56:11 |
| 200.65.129.2:3128 | 1.5230 | Transp. | MX | Y | 100% | 2009-06-14 11:14:10 |
| 82.117.50.16:80 | 1.5250 | Transp. | NO | Y | 100% | 2009-06-14 11:14:10 |
| 88.191.94.176:3128 | 1.5720 | Transp. | FR | Y | 74% | 2009-06-14 11:14:10 |
| 69.30.227.98:3128 | 1.5920 | Transp. | US | Y | 78% | 2009-06-14 11:14:10 |
| 89.202.211.28:3128 | 1.6470 | Transp. | GB | Y | 96% | 2009-06-14 11:14:10 |
| 87.246.50.246:8080 | 1.6560 | Transp. | BG | Y | 63% | 2009-06-14 11:14:10 |
| 219.8.4.2:1080 | 1.6710 | Elite | JP | ? | 22% | 2009-06-14 10:53:11 |
| 200.65.127.161:3128 | 1.6760 | Transp. | MX | N | 100% | 2009-06-14 11:14:10 |
| 200.164.117.106:3128 | 1.6900 | Transp. | BR | Y | 100% | 2009-06-14 11:14:10 |
| 78.41.16.23:3128 | 1.6970 | Transp. | CZ | Y | 59% | 2009-06-14 11:14:10 |
| 77.70.86.54:808 | 1.7280 | Elite | BG | Y | 53% | 2009-06-14 10:53:11 |
| 65.42.208.146:8080 | 1.7570 | Transp. | US | Y | 60% | 2009-06-14 11:14:10 |
| 201.91.211.2:80 | 1.7810 | Transp. | BR | Y | 98% | 2009-06-14 11:14:10 |
| 200.30.101.109:8080 | 1.7950 | Transp. | CR | Y | 42% | 2009-06-14 11:14:10 |
| 201.53.100.127:3128 | 1.8060 | Transp. | BR | Y | 99% | 2009-06-14 11:14:10 |
| 189.21.192.74:8080 | 1.8110 | Transp. | BR | ? | 100% | 2009-06-14 11:14:10 |
| 200.223.225.129:8080 | 1.8240 | Transp. | BR | Y | 99% | 2009-06-14 11:14:10 |
| 200.196.242.143:3128 | 1.8360 | Transp. | BR | Y | 95% | 2009-06-14 11:14:10 |
GooD LucK !

Please add your comment !
>Special Security
Protect Your PayPal Account from Hackers
Learn how to keep out hackers your PayPal account. With the ever growing popularity of PayPal, there are always people that want your money.
Protect Your PayPal Account by NEVER Opening Paypal Emails
One popular way that hackers are accessing PayPal is through email. Most people already know NOT to click a link in an email for their PayPal mail. Fake emails are supposed to be sent to spoof@ PayPal.com.
Do NOT ever open emails from PayPal. Do not open mails to see that a transaction occurred. Do not open mails that show you paid or anything. Everything that you need for financial record keeping for PayPal can be accessed directly from the PayPal site. You can print transaction logs directly from the PayPal site. You can print individual receipts from purchases and subscription payments directly from the site.
There is a hacker program that once you open an email, the program automatically retrieves your email password. Without your knowledge, the hacker sends a request to PayPal for lost password. PayPal then sends the new password information to the email. The hacker has your email password and can then automatically retrieve your PayPal password without your knowledge.
Keep the PayPal customer service number available. If an email has been received that the PayPal account has been compromised, it is best to talk to the customer service representatives instead of communicating via emails and on the PayPal site. Some emails state that the account has been compromised so that you will open that email. Once the email is opened it might be too late. These spoof emails are designed to create a panic and get you to click links inside the email. But the info that the hacker needs is given to them as soon as you open the email. Clicking the link just makes their job easier.
Protect Your PayPal Account by Calling Customer Service
If you open an email, call the PayPal customer service immediately. Tell them that your account was compromised. Ask for assistance on temporarily freezing the account until you can secure it again. Get the PayPal staff to help you secure your account.
Way to detect who is spying you
GETTING SUM1'S IP Address How HAS Hacked Your PC First
open dos command,go to -(Start/Run/type "command" without inverted commas and hit enter),& in the MSDOS prompt,type:
netstat -a
(make sure you include the space in between the "t" and the "-a").
This command will show u the host name of the lamer and of course yours also ..your host name will be under local address and his wud be under foreign address.. note any suspicious name and every number u c after the host name under foreign address which is new and suspicious there(numbers are ports but i consider u totally unaware).
After ur done,now type
Netstat -an (again a space between "t" and "-an")
this will list all connections in numerical form, which makes it a lot easier to trace malicious users....Hostnames can be a little confusing if you don't know what you're doing (although they're easily understandable, as we shall see later). Also, by doing this, you can also find out what your own IP address is, which is always useful.
It wud look a bit like this
A New IP:Port -note that stuff
Now that you have a IP Address and a host name,type
tracert type IP address/Hostname here
write whole thing there.. that's after you write tracert give a space then type A New IP we found in last step.. give a / then write..Host name we found in first step.remember no port there to be added..
This will trace the lamer which is prolly using a Trojan on your computer to do what he wants..result will give u some ip addresses ..note all of them
now go to ip2location.com/free.asp
write ip addresses in the box and see where the ips belong to..some ips will give u ISPs like mtnl ... last IP wud be his IP ..now call Your or his ISP & inform dem abt it!DO RESPOND 2 DIS..
->Special Security Team
Windows Anti-Debug Reference
This paper classifies and presents several anti-debugging techniques used on Windows NT-based operating systems. Anti-debugging techniques are ways for a program to detect if it runs under control of a debugger. They are used by commercial executable protectors, packers and malicious software, to prevent or slow-down the process of reverse-engineering. We'll suppose the program is analyzed under a ring3 debugger, such as OllyDbg on Windows platforms. The paper is aimed towards reverse-engineers and malware analysts. Note that we will talk purely about generic anti-debugging and anti-tracing techniques. Specific debugger detection, such as window or processes enumeration, registry scanning, etc. will not be addressed here.
[1] IntroThis paper classifies and presents several anti-debugging techniques used on Windows NT-based operating systems.
Anti-debugging techniques are ways for a program to detect if it runs under control of a debugger. They are used by commercial executable protectors, packers and malicious software, to prevent or slow-down the process of reverse-engineering.
We'll suppose the program is analyzed under a ring3 debugger, such as OllyDbg on Windows platforms. The paper is aimed towards reverse-engineers and malware analysts.
Note that we will talk purely about generic anti-debugging and anti-tracing techniques. Specific debugger detection, such as window or processes enumeration, registry scanning, etc. will not be addressed here.
[2] Anti-debugging and anti-tracing techniques
- Exploiting memory discrepancies
(1) kernel32!IsDebuggerPresent
IsDebuggerPresent returns 1 if the process is being debugged, 0 otherwise. This API simply reads the PEB!BeingDebugged byte-flag (located at offset 2 in the PEB structure).
Circumventing it is as easy as setting PEB!BeingDebugged to 0.
Example:
call IsDebuggerPresent
test eax, eax
jne @DebuggerDetected
...
(2) PEB!IsDebugged
This field refers to the second byte in the Process Environment Block of the process. It is set by the system when the process is debugged.
This byte can be reset to 0 without consequences for the course of execution of the program (it is an informative flag).
Example:
mov eax, fs:[30h]
mov eax, byte [eax+2]
test eax, eax
jne @DebuggerDetected
...
(3) PEB!NtGlobalFlags
When a process is created, the system sets some flags that will define how various APIs will behave for this program. Those flags can be read in the PEB, in the DWORD located at offset 0x68 (see the reference).
By default, different flags are set depending if the process is created under a debugger or not. If the process is debugged, some flags controlling the heap manipulation routines in ntdll will be set: FLG_HEAP_ENABLE_TAIL_CHECK, FLG_HEAP_ENABLE_FREE_CHECK and FLG_HEAP_VALIDATE_PARAMETERS.
This anti-debug can be bypassed by resetting the NtGlobalFlags field.
Example:
mov eax, fs:[30h]
mov eax, [eax+68h]
and eax, 0x70
test eax, eax
jne @DebuggerDetected
...
(4) Heap flags
As explained previously, NtGlobalFlags informs how the heap routines will behave (among other things). Though it is easy to modify the PEB field, if the heap does not behave the same way as it should when the process is not debugged, this could be problematic. It is a powerful anti-debug, as process heaps are numerous, and their chunks can be individually affected by the FLG_HEAP_* flags (such as chunk tails). Heap headers would be affected as well. For instance, checking the field ForceFlags in a heap header (offset 0x10) can be used to detect the presence of a debugger.
There are two easy ways to circumvent it:
- Create a non-debugged process, and attach the debugger once the process has been created (an easy solution is to create the process suspended, run until the entry-point is reached, patch it to an infinite loop, resume the process, attach the debugger, and restore the original entry-point).
- Force the NtGlobalFlags for the process that we want to debug, via the registry key "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options": Create a subkey (not value) named as your process name, and under this subkey, a String value "GlobalFlags" set to nothing.
Example:
mov eax, fs:[30h]
mov eax, [eax+18h] ;process heap
mov eax, [eax+10h] ;heap flags
test eax, eax
jne @DebuggerDetected
...
(5) Vista anti-debug (no name)
Here's an anti-debug specific to Windows Vista that I found by comparing memory dumps of a program running with and without control of a debugger. I'm not sure of its realiability, but it's worth mentionning (tested on Windows Vista 32 bits, SP0, English version).
When a process is debugged, its main thread TEB, at offset 0xBFC, contains a pointer to a unicode string referencing a system dll. Moreover, the string follows this pointer (therefore, located at offset 0xC00 in the TEB). If the process is not debugged, the pointer is set to NULL and the string is not present.
Example:
call GetVersion
cmp al, 6
jne @NotVista
push offset _seh
push dword fs:[0]
mov fs:[0], esp
mov eax, fs:[18h] ; teb
add eax, 0BFCh
mov ebx, [eax] ; pointer to a unicode string
test ebx, ebx ; (ntdll.dll, gdi32.dll,...)
je @DebuggerNotFound
sub ebx, eax ; the unicode string follows the
sub ebx, 4 ; pointer
jne @DebuggerNotFound
;debugger detected if it reaches this point
;...
- Exploiting system discrepancies
(1) NtQueryInformationProcess
ntdll!NtQueryInformationProcess is a wrapper around the ZwQueryInformationProcess syscall. Its prototype is the following:
NTSYSAPI NTSTATUS NTAPI NtQueryInformationProcess(
IN HANDLE ProcessHandle,
IN PROCESS_INFORMATION_CLASS ProcessInformationClass,
OUT PVOID ProcessInformation,
IN ULONG ProcessInformationLength,
OUT PULONG ReturnLength
);
When called with ProcessInformationClass set to 7 (ProcessDebugPort constant), the system will set ProcessInformation to -1 if the process is debugged.
It is a powerful anti-debug, and there is no easy way to circumvent it. However, if the program is traced, ProcessInformation can be modified when the syscall returns.
Another solution is to use a system driver that would hook the ZwNtQueryInformationProcess syscall.
Circumventing NtQueryInformationProcess will bypass many anti-debug techniques (such as CheckRemoteDebuggerPresent or UnhandledExceptionFilter).
Example:
push 0
push 4
push offset isdebugged
push 7 ;ProcessDebugPort
push -1
call NtQueryInformationProcess
test eax, eax
jne @ExitError
cmp isdebugged, 0
jne @DebuggerDetected
...
(2) kernel32!CheckRemoteDebuggerPresent
This API takes two parameters: a process handle, and a pointer to a DWORD. If the call is successful, the DWORD value will be set to 1 if the process is being debugged.
Internally, this API calls ntdll!NtQueryInformationProcess with ProcessInformationClass set to ProcessDebugPort (7).
Example:
push offset isdebugged
push -1
call CheckRemoteDebuggerPresent
test eax, eax
jne @DebuggerDetected
...
(3) UnhandledExceptionFilter
When an exception occurs, with Windows XP SP>=2, Windows 2003, and Windows Vista, the usual way the OS processes the exception is:
- If any, pass control to the per-process Vectored Exception Handlers.
- If the exception is not processed, pass the control to the per-thread top SEH handler, pointed by FS:[0] in the thread that generated the exception. SEH are chained and called in turn if the exception is not processed by the previous in the chain.
- If the exception has not been processed by any of the previous handlers, the final SEH handler (set by the system), will call kernel32!UnhandledExceptionFilter. This function will decide what it should do depending if the process is debugged or not.
- If it is not debugged, it will call the user-defined filter function (set via kernel32!SetUnhandledExceptionFilter).
- If it debugged, the program will be terminated.
The debugger detection in UnhandledExceptionFilter is made with ntdll!NtQueryInformationProcess.
Example:
push @not_debugged
call SetUnhandledExceptionFilter
xor eax, eax
mov eax, dword [eax] ; trigger exception
;program terminated if debugged
;...
@not_debugged:
;process the exception
;continue the execution
;...
(4) NtSetInformationThread
ntdll!NtSetInformationThread is a wrapper around the ZwSetInformationThread syscall. Its prototype is the following:
NTSYSAPI NTSTATUS NTAPI NtSetInformationThread(
IN HANDLE ThreadHandle,
IN THREAD_INFORMATION_CLASS ThreadInformationClass,
IN PVOID ThreadInformation,
IN ULONG ThreadInformationLength
);
When called with ThreadInformationClass set to 0x11 (ThreadHideFromDebugger constant), the thread will be detached from the debugger.
Similarly to ZwQueryInformationProcess, circumventing this anti-debug requires either modifying ZwSetInformationThread parameters before it's called, or hooking the syscall directly with the use of a kernel driver.
Example:
push 0
push 0
push 11h ;ThreadHideFromDebugger
push -2
call NtSetInformationThread
;thread detached if debugged
;...
(5) kernel32!CloseHandle and NtClose
APIs making user of the ZwClose syscall (such as CloseHandle, indirectly) can be used to detect a debugger. When a process is debugged, calling ZwClose with an invalid handle will generate a STATUS_INVALID_HANDLE (0xC0000008) exception.
As with all anti-debugs that rely on information made directly available from the kernel (therefore involving a syscall), the only proper way to bypass the "CloseHandle" anti-debug is to either modify the syscall data from ring3, before it is called, or set up a kernel hook.
This anti-debug, though extremely powerful, does not seem to be widely used by malicious programs.
Example:
push offset @not_debugged
push dword fs:[0]
mov fs:[0], esp
push 1234h ;invalid handle
call CloseHandle
; if fall here, process is debugged
;...
@not_debugged:
;...
(6) Self-debugging
A process can detect it is being debugged by trying to debug itself, for instance by creating a new process, and calling kernel32!DebugActiveProcess(pid) on the parent process.
In turn, this API calls ntdll!DbgUiDebugActiveProcess which will call the syscall ZwDebugActiveProcess. If the process is already debugged, the syscall fails. Note that retrieving the parent process PID can be done with the toolhelp32 APIs (field th32ParentProcessID in the PROCESSENTRY32 structure.
(7) Kernel-mode timers
kernel32!QueryPerformanceCounter is an efficent anti-debug. This API calls ntdll!NtQueryPerformanceCounter which wraps the ZwQueryPerformanceCounter syscall.
Again, there is no easy way to circumvent this anti-tracing trick.
(8) User-mode timers
An API such as kernel32!GetTickCount returns the number of milliseconds ellapsed since the system started. The interesting thing is that it does not make use of kernel-related service to perform its duties. A user-mode process has this counter mapped in its address space. For 8Gb user-mode spaces, the value returned would be:
d[0x7FFE0000] * d[0x7FFE0004] / (2^24)
(9) kernel32!OutputDebugStringA
This anti-debug is quite original, I have encountered it only once, in files packed with ReCrypt v0.80. The trick consists of calling OutputDebugStringA, with a valid ASCII string. If the program is run under control of a debugger, the return value will be the address of the string passed as a parameter. In normal conditions, the return value should be 1.
Example:
xor eax, eax
push offset szHello
call OutputDebugStringA
cmp eax, 1
jne @DebuggerDetected
...
(10) Ctrl-C
When a console program is debugged, a Ctrl-C signal will throw a EXCEPTION_CTL_C exception, whereas the signal handler would be called directly is the program is not debugged.
Example:
push offset exhandler
push 1
call RtlAddVectoredExceptionHandler
push 1
push sighandler
call SetConsoleCtrlHandler
push 0
push CTRL_C_EVENT
call GenerateConsoleCtrlEvent
push 10000
call Sleep
push 0
call ExitProcess
exhandler:
;check if EXCEPTION_CTL_C, if it is,
;debugger detected, should exit process
;...
sighandler:
;continue
;...
- CPU anti-debug
(1) Rogue Int3
This is a classic anti-debug to fool weak debuggers. It consists of inserting an INT3 opcode in the middle of a valid sequence of instructions. When the INT3 is executed, if the program is not debugged, control will be given to the exception handler of the protection and execution will continue.
As INT3 instructions are used by debuggers to set software breakpoints, inserting INT3 opcodes can be used to trick the debugger into believing that it is one his breakpoints. Therefore, the control would not be given to the exception handler, and the course of the program would be modified. Debuggers should track where they set software breakpoints to avoid falling for this one.
Similarly, note that INT3 may be encoded as 0xCD, 0x03.
Example:
push offset @handler
push dword fs:[0]
mov fs:[0], esp
;...
db 0CCh
;if fall here, debugged
;...
@handler:
;continue execution
;...
(2) "Ice" Breakpoint
The so-called "Ice breakpoint" is one of Intel's undocumented instruction, opcode 0xF1. It is used to detect tracing programs.
Executing this instruction will generate a SINGLE_STEP exception. Therefore, if the program is already traced, the debugger will think it is the normal exception generated by executing the instruction with the SingleStep bit set in the Flags registers. The associated exception handler won't be executed, and execution will not continue as expected.
Bypassing this trick is easy: one can run over the instruction, instead and single-stepping on it. The exception will be generated, but since the program is not traced, the debugger should understand that it has to pass control to the exception handler.
Example:
push offset @handler
push dword fs:[0]
mov fs:[0], esp
;...
db 0F1h
;if fall here, traced
;...
@handler:
;continue execution
;...
(3) Interrupt 2Dh
Executing this interrupt if the program is not debugged will raise a breakpoint exception. If the program is debugged, and the instruction is not executed with the trace flag, no exception will be generated, and execution will carry on normally. If the program is debugged and the instruction traced, the following byte will be skipped, and execution will continue. Therefore, using INT 2Dh can be used as a powerful anti-debug and anti-tracer mechanism.
Example:
push offset @handler
push dword fs:[0]
mov fs:[0], esp
;...
db 02Dh
mov eax, 1 ;anti-tracing
;...
@handler:
;continue execution
;...
(4) Timestamp counters
High precision counters, storing the current number of CPU cycles executed since the machine started, can be queried with the RDTSC instruction. Classic anti-debugs consist of measuring time deltas at key points in the program, usually around exception handlers. If the delta is too large, that would mean the program runs under control of a debugger (processing the exception in the debugger, and giving control back to the debuggee is a lengthy task).
Example:
push offset handler
push dword ptr fs:[0]
mov fs:[0],esp
rdtsc
push eax
xor eax, eax
div eax ;trigger exception
rdtsc
sub eax, [esp] ;ticks delta
add esp, 4
pop fs:[0]
add esp, 4
cmp eax, 10000h ;threshold
jb @not_debugged
@debugged:
...
@not_debugged:
...
handler:
mov ecx, [esp+0Ch]
add dword ptr [ecx+0B8h], 2 ;skip div
xor eax, eax
ret
(5) Popf and the trap flag
The trap flag, located in the Flags register, controls the tracing of a program. If this flag is set, executing an instruction will also raise a SINGLE_STEP exception. The trap flag can be manipulated in order to thwart tracers. For instance, this sequence of instructions will set the trap flag:
pushf
mov dword [esp], 0x100
popf
If the program is being traced, this will have no real effect on the flags register, and the debugger will process the exception, believing it comes from regular tracing. The exception handler won't be executed. Circumventing this anti-tracer trick simply require to run over the pushf instruction.
(6) Stack Segment register
Here's a very original anti-tracer. I encountered it in a packer called MarCrypt. I believe it is not widely known, not to mention, used.
It consists of tracing over this sequence of instructions:
push ss
pop ss
pushf
nop
When tracing over pop ss, the next instruction will be executed but the debugger will not break on it, therefore stopping on the following instruction (NOP in this case).
Marcrypt uses this anti-debug the following way:
push ss
; junk
pop ss
pushf
; junk
pop eax
and eax, 0x100
or eax, eax
jnz @debugged
; carry on normal execution
The trick here is that, if the debugger is tracing over that sequence of instructions, popf will be excuted implicitly, and the debugger will not be able to unset the trapflag in the pushed value on the stack. The protection checks for the trap flag and terminates the program if it's found.
One simple way to circumvent this anti-tracing is to breakpoint on popf and run the program (to avoid using the TF flag).
(7) Debug registers manipulation
Debug registers (DR0 through DR7) are used to set hardware breakpoints. A protection can manipulate them to either detect that hardware breakpoints have been set (and therefore, that it is being debugged), reset them or set them to particular values used to perform code checks later. A packer such as tElock makes use of the debug registers to prevent reverse-engineers from using them.
From a user-mode perspective, debug registers cannot be set using the privileged 'mov drx, ...' instruction. Other ways exist:
- An exception can be generated, the thread context modified (it contains the CPU registers at the time the exception was thrown), and then resumed to normal execution with the new context.
- The other way is to use the NtGetContextThread and NtSetContextThread syscalls (available in kernel32 with GetThreadContext and SetThreadContext).
Most protectors use the first, "unofficial" way.
Example:
push offset handler
push dword ptr fs:[0]
mov fs:[0],esp
xor eax, eax
div eax ;generate exception
pop fs:[0]
add esp, 4
;continue execution
;...
handler:
mov ecx, [esp+0Ch] ;skip div
add dword ptr [ecx+0B8h], 2 ;skip div
mov dword ptr [ecx+04h], 0 ;clean dr0
mov dword ptr [ecx+08h], 0 ;clean dr1
mov dword ptr [ecx+0Ch], 0 ;clean dr2
mov dword ptr [ecx+10h], 0 ;clean dr3
mov dword ptr [ecx+14h], 0 ;clean dr6
mov dword ptr [ecx+18h], 0 ;clean dr7
xor eax, eax
ret
(8) Context modification
As with debug registers manipulation, the context can also be used to modify in an unconventionnal way the execution stream of a program. Debuggers can get easily confused!
Note that another syscall, NtContinue, can be used to load a new context in the current thread (for instance, this syscall is used by the exception handler manager).
- Uncategorized anti-debug
(1) TLS-callback
This anti-debug was not so well-known a few years ago. It consists to instruct the PE loader that the first entry point of the program is referenced in a Thread Local Storage entry (10th directory entry number in the PE optional header). By doing so, the program entry-point won't be executed first. The TLS entry can then perform anti-debug checks in a stealthy way.
Note that in practice, this technique is not widely used.
Though older debuggers (including OllyDbg) are not TLS-aware, counter-measures are quite easy to take, by the means of plugins of custom patcher tools.
(2) CC scanning
A common protection feature used by packers is the CC-scanning loop, aimed at detecting software breakpoints set by a debugger. If you want to avoid that kind of troubles, you may want to use either hardware breakpoints or a custom type of software breakpoint. CLI (0xFA) is a good candidate to replace the classic INT3 opcode. This instruction does have the requirements for the job: it raises a privileged instruction exception if executed by a ring3 program, and occupies only 1 byte of space.
(3) EntryPoint RVA set to 0
Some packed files have their entry point RVA set to 0, which means they will start executing 'MZ...' which corresponds to 'dec ebx / pop edx ...'.
This is not an anti-debug trick in itself, but can be annoying if you want to break on the entry-point by using a software breakpoint.
If you create a suspended process, then set an INT3 at RVA 0, you will erase part of the magic MZ value ('M'). The magic was checked when the process was created, but it will get checked again by ntdll when the process is resumed (in the hope of reaching the entry-point). In that case, an INVALID_IMAGE_FORMAT exception will be raised.
If you create your own tracing or debugging tool, you will want to use hardware breakpoint to avoid this problem.
[3] Conclusion
Knowing anti-debugging and anti-tracing techniques (un)commonly used by malware or protectors is useful knowledge for a reverse-engineer. A program will always have ways to find it is run in a debugger - the same applies for virtual or emulated environments, but since ring3 debuggers are some of the most common analysis tools used, knowing common tricks, and how to bypass them, will always prove useful.
[4] Links
MSDN
Portable Executable Tutorial, Matt Pietrek
Syscall Reference, The Metasploit Project
Undocumented Functions for MS Windows NT/2K
Intel Manuals
- Common exception codes - Microsoft Windows SDK, ntdll.h
- Status codes list (including common exception codes) - Microsoft Windows DDK, ntstatus.h
- Context Structures documentation - Microsoft Windows SDK, ntdll.h
[5] Data reference
- CONTEXT structure for IA32 processors
struct CONTEXT_IA32
{
// ContextFlags must be set to the appropriate CONTEXT_* flag
// before calling (Set|Get)ThreadContext
DWORD ContextFlags;
// CONTEXT_DEBUG_REGISTERS (not included in CONTEXT_FULL)
DWORD Dr0; // 04h
DWORD Dr1; // 08h
DWORD Dr2; // 0Ch
DWORD Dr3; // 10h
DWORD Dr6; // 14h
DWORD Dr7; // 18h
// CONTEXT_FLOATING_POINT
FLOATING_SAVE_AREA FloatSave;
// CONTEXT_SEGMENTS
DWORD SegGs; // 88h
DWORD SegFs; // 90h
DWORD SegEs; // 94h
DWORD SegDs; // 98h
// CONTEXT_INTEGER
DWORD Edi; // 9Ch
DWORD Esi; // A0h
DWORD Ebx; // A4h
DWORD Edx; // A8h
DWORD Ecx; // ACh
DWORD Eax; // B0h
// CONTEXT_CONTROL
DWORD Ebp; // B4h
DWORD Eip; // B8h
DWORD SegCs; // BCh (must be sanitized)
DWORD EFlags; // C0h
DWORD Esp; // C4h
DWORD SegSs; // C8h
// CONTEXT_EXTENDED_REGISTERS (processor-specific)
BYTE ExtendedRegisters[MAXIMUM_SUPPORTED_EXTENSION];
};
- Process Environment Block structure (from The Wine Project)
struct PEB
{
BOOLEAN InheritedAddressSpace; // 00
BOOLEAN ReadImageFileExecOptions; // 01
BOOLEAN BeingDebugged; // 02
BOOLEAN SpareBool; // 03
HANDLE Mutant; // 04
HMODULE ImageBaseAddress; // 08
PPEB_LDR_DATA LdrData; // 0c
RTL_UPROCESS_PARAMETERS *ProcessParameters; // 10
PVOID SubSystemData; // 14
HANDLE ProcessHeap; // 18
PRTL_CRITICAL_SECTION FastPebLock; // 1c
PVOID /*PPEBLOCKROUTI*/ FastPebLockRoutine; // 20
PVOID /*PPEBLOCKROUTI*/ FastPebUnlockRoutine; // 24
ULONG EnvironmentUpdateCount; // 28
PVOID KernelCallbackTable; // 2c
PVOID EventLogSection; // 30
PVOID EventLog; // 34
PVOID /*PPEB_FREE_BLO*/ FreeList; // 38
ULONG TlsExpansionCounter; // 3c
PRTL_BITMAP TlsBitmap; // 40
ULONG TlsBitmapBits[2]; // 44
PVOID ReadOnlySharedMemoryBase; // 4c
PVOID ReadOnlySharedMemoryHeap; // 50
PVOID *ReadOnlyStaticServerData; // 54
PVOID AnsiCodePageData; // 58
PVOID OemCodePageData; // 5c
PVOID UnicodeCaseTableData; // 60
ULONG NumberOfProcessors; // 64
ULONG NtGlobalFlag; // 68
BYTE Spare2[4]; // 6c
LARGE_INTEGER CriticalSectionTimeout; // 70
ULONG HeapSegmentReserve; // 78
ULONG HeapSegmentCommit; // 7c
ULONG HeapDeCommitTotalFreeTh; // 80
ULONG HeapDeCommitFreeBlockTh; // 84
ULONG NumberOfHeaps; // 88
ULONG MaximumNumberOfHeaps; // 8c
PVOID *ProcessHeaps; // 90
PVOID GdiSharedHandleTable; // 94
PVOID ProcessStarterHelper; // 98
PVOID GdiDCAttributeList; // 9c
PVOID LoaderLock; // a0
ULONG OSMajorVersion; // a4
ULONG OSMinorVersion; // a8
ULONG OSBuildNumber; // ac
ULONG OSPlatformId; // b0
ULONG ImageSubSystem; // b4
ULONG ImageSubSystemMajorVersion; // b8
ULONG ImageSubSystemMinorVersion; // bc
ULONG ImageProcessAffinityMask; // c0
ULONG GdiHandleBuffer[34]; // c4
ULONG PostProcessInitRoutine; // 14c
PRTL_BITMAP TlsExpansionBitmap; // 150
ULONG TlsExpansionBitmapBits[32]; // 154
ULONG SessionId; // 1d4
};
- Thread Environment Block structure (from The Wine Project)
struct TEB
{
NT_TIB Tib; // 000 Info block
PVOID EnvironmentPointer; // 01c
CLIENT_ID ClientId; // 020 PID,TID
PVOID ActiveRpcHandle; // 028
PVOID ThreadLocalStoragePointer; // 02c
PEB *Peb; // 030
DWORD LastErrorValue; // 034
ULONG CountOfOwnedCriticalSections; // 038
PVOID CsrClientThread; // 03c
PVOID Win32ThreadInfo; // 040
ULONG Win32ClientInfo[0x1f]; // 044
PVOID WOW32Reserved; // 0c0
ULONG CurrentLocale; // 0c4
ULONG FpSoftwareStatusRegister; // 0c8
PVOID SystemReserved1[54]; // 0cc
PVOID Spare1; // 1a4
LONG ExceptionCode; // 1a8
BYTE SpareBytes1[40]; // 1ac
PVOID SystemReserved2[10]; // 1d4
DWORD num_async_io; // 1fc
ULONG_PTR dpmi_vif; // 200
DWORD vm86_pending; // 204
DWORD pad6[309]; // 208
ULONG gdiRgn; // 6dc
ULONG gdiPen; // 6e0
ULONG gdiBrush; // 6e4
CLIENT_ID RealClientId; // 6e8
HANDLE GdiCachedProcessHandle; // 6f0
ULONG GdiClientPID; // 6f4
ULONG GdiClientTID; // 6f8
PVOID GdiThreadLocaleInfo; // 6fc
PVOID UserReserved[5]; // 700
PVOID glDispachTable[280]; // 714
ULONG glReserved1[26]; // b74
PVOID glReserved2; // bdc
PVOID glSectionInfo; // be0
PVOID glSection; // be4
PVOID glTable; // be8
PVOID glCurrentRC; // bec
PVOID glContext; // bf0
ULONG LastStatusValue; // bf4
UNICODE_STRING StaticUnicodeString; // bf8
WCHAR StaticUnicodeBuffer[261]; // c00
PVOID DeallocationStack; // e0c
PVOID TlsSlots[64]; // e10
LIST_ENTRY TlsLinks; // f10
PVOID Vdm; // f18
PVOID ReservedForNtRpc; // f1c
PVOID DbgSsReserved[2]; // f20
ULONG HardErrorDisabled; // f28
PVOID Instrumentation[16]; // f2c
PVOID WinSockData; // f6c
ULONG GdiBatchCount; // f70
ULONG Spare2; // f74
ULONG Spare3; // f78
ULONG Spare4; // f7c
PVOID ReservedForOle; // f80
ULONG WaitingOnLoaderLock; // f84
PVOID Reserved5[3]; // f88
PVOID *TlsExpansionSlots; // f94
};
- NtGlobalFlags
FLG_STOP_ON_EXCEPTION 0x00000001
FLG_SHOW_LDR_SNAPS 0x00000002
FLG_DEBUG_INITIAL_COMMAND 0x00000004
FLG_STOP_ON_HUNG_GUI 0x00000008
FLG_HEAP_ENABLE_TAIL_CHECK 0x00000010
FLG_HEAP_ENABLE_FREE_CHECK 0x00000020
FLG_HEAP_VALIDATE_PARAMETERS 0x00000040
FLG_HEAP_VALIDATE_ALL 0x00000080
FLG_POOL_ENABLE_TAIL_CHECK 0x00000100
FLG_POOL_ENABLE_FREE_CHECK 0x00000200
FLG_POOL_ENABLE_TAGGING 0x00000400
FLG_HEAP_ENABLE_TAGGING 0x00000800
FLG_USER_STACK_TRACE_DB 0x00001000
FLG_KERNEL_STACK_TRACE_DB 0x00002000
FLG_MAINTAIN_OBJECT_TYPELIST 0x00004000
FLG_HEAP_ENABLE_TAG_BY_DLL 0x00008000
FLG_IGNORE_DEBUG_PRIV 0x00010000
FLG_ENABLE_CSRDEBUG 0x00020000
FLG_ENABLE_KDEBUG_SYMBOL_LOAD 0x00040000
FLG_DISABLE_PAGE_KERNEL_STACKS 0x00080000
FLG_HEAP_ENABLE_CALL_TRACING 0x00100000
FLG_HEAP_DISABLE_COALESCING 0x00200000
FLG_VALID_BITS 0x003FFFFF
FLG_ENABLE_CLOSE_EXCEPTION 0x00400000
FLG_ENABLE_EXCEPTION_LOGGING 0x00800000
FLG_ENABLE_HANDLE_TYPE_TAGGING 0x01000000
FLG_HEAP_PAGE_ALLOCS 0x02000000
FLG_DEBUG_WINLOGON 0x04000000
FLG_ENABLE_DBGPRINT_BUFFERING 0x08000000
FLG_EARLY_CRITICAL_SECTION_EVT 0x10000000
FLG_DISABLE_DLL_VERIFICATION 0x80000000
By Dr.^Y^.0pt!X










![[2a6jvpg.jpg.gif]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh3DeVwIT-rEycs4ctNT_UgpN21U1q3RdP9EXdVwqjokQY4NqnNBpYGQiHOjnWQmglOPKSDXY6-kcRpma2OHgAGCcZc7kWrO1NJ_P2oNHWWiuVXxaWw9f9idyRfLbvfdpxZ5xb3hKMl6nnS/s1600/2a6jvpg.jpg.gif)
![[Specialsecurity.gif]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiHdW_yAzCMaTqyzMc0_GRFdQ2xE-zzIl8mKdce4euar70R1CDH8hMM17hcOv5KWTrHQdt7CCPpbTzOPQAahU72e-UmyHSii9pkIOZV0ETPdrnKo21UgGYExqIqkuBgWNMZ7YEX47bSUCKa/s1600/Specialsecurity.gif)














